Understanding Public EC2 vs. NAT Gateway in AWS
When building your applications in AWS, you might find yourself pondering a crucial question: Should I use an Internet Gateway (IGW) or a NAT Gateway (NGW)? While both options enable internet communication, they serve different purposes and have unique security implications. Let's explore these gateways, understand their paths, and see what they mean for your cloud security.
Public EC2: A Path for Public Communication
An Internet Gateway (IGW) is your VPC's door to the internet. It allows resources within a public subnet to communicate directly with the outside world.
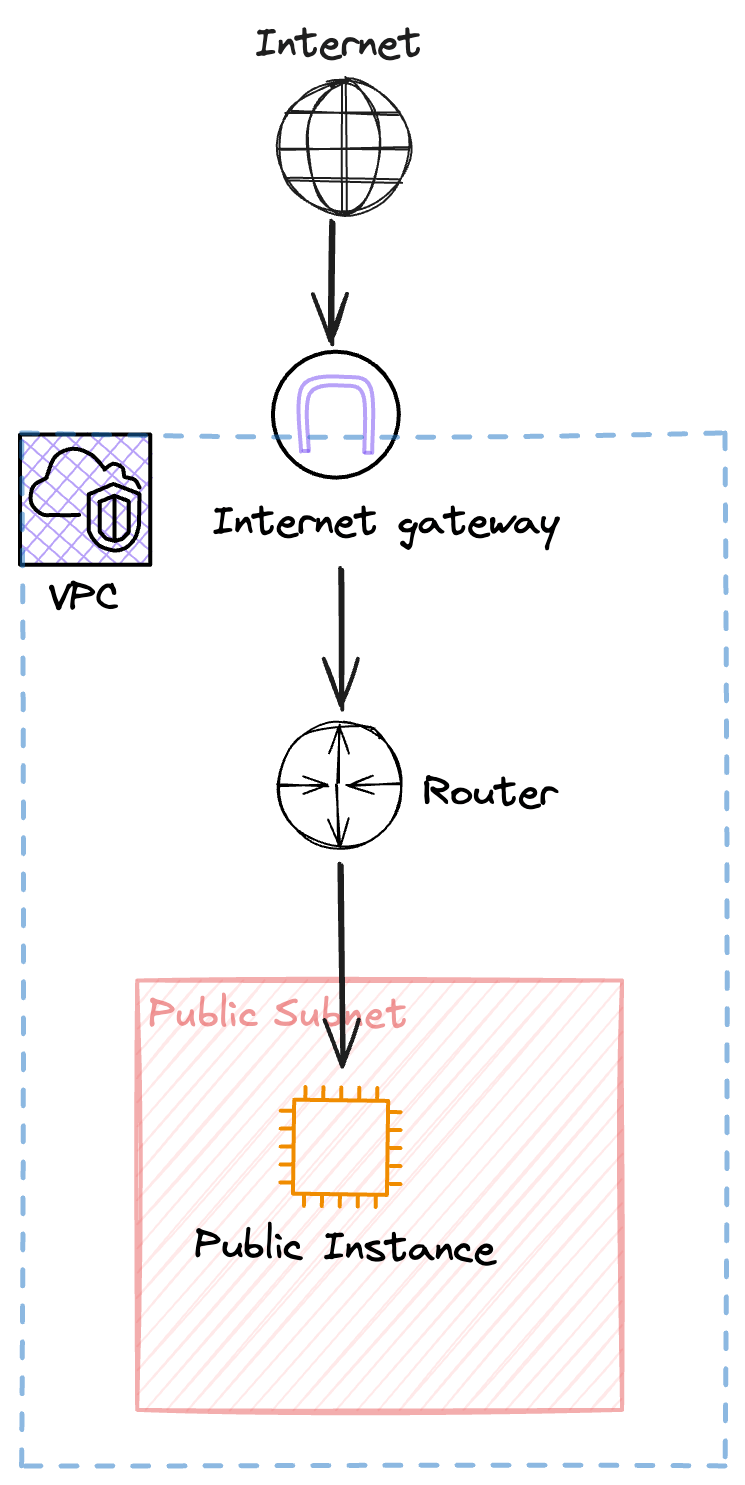
How It Works:
Imagine the following path:
- VPC: Your isolated network environment in AWS.
- Router: Directs traffic between subnets and the internet.
- Internet Gateway: Bridges your VPC to the internet.
- Public Subnet: Houses resources like EC2 instances with public or Elastic IPs.
- Route Table: Routes internet-bound traffic (
0.0.0.0/0) through the IGW.
Example Use Case:
- Hosting a public-facing web server on an EC2 instance that serves your website or application to users worldwide.
Security Considerations:
- Security Groups: Configure to allow inbound traffic only from trusted IPs or on specific ports (like 80 for HTTP and 443 for HTTPS).
- Network ACLs (NACLs): Add an extra layer of defense by controlling traffic to and from subnets.
- Public Exposure: Since resources have public IPs, they are visible to the internet, making them potential targets. Implement strong access controls and continuous monitoring.
NAT Gateway: Enabling Outbound-Only Communication
A NAT Gateway (NGW) allows resources in a private subnet to access the internet for outbound communication without exposing them to inbound internet traffic.
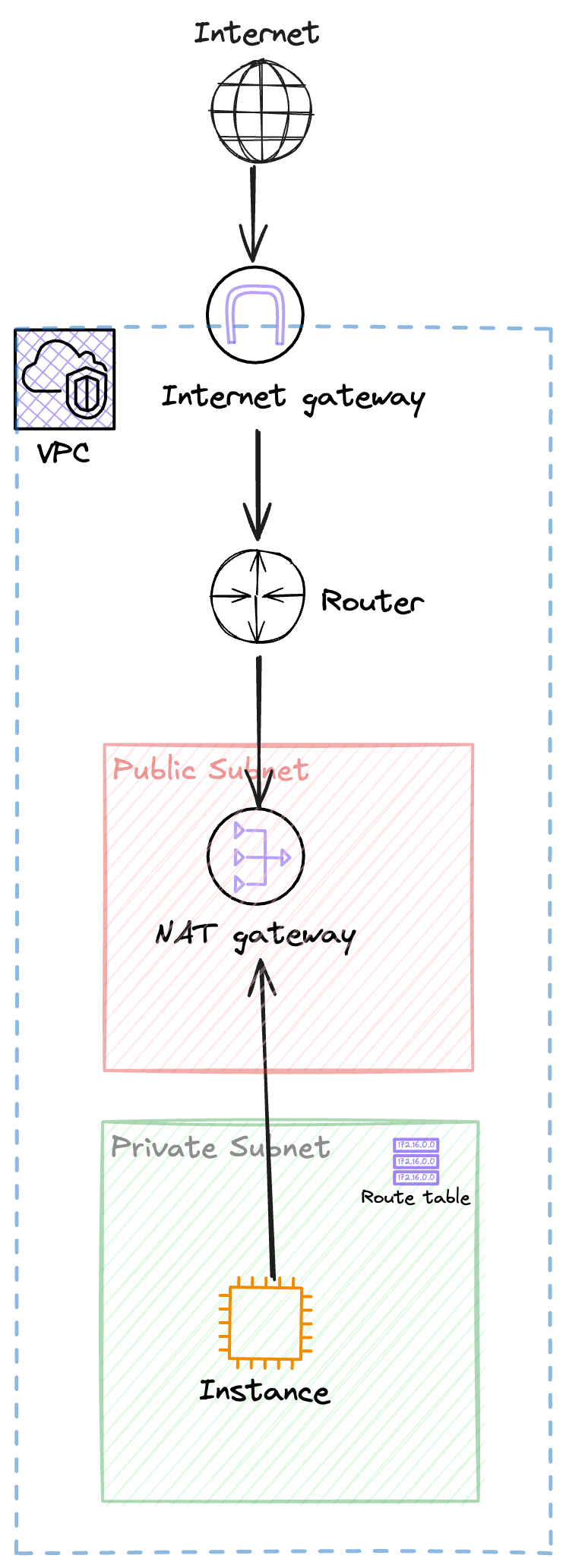
How It Works:
Consider this path:
- VPC: Contains both your public and private subnets.
- Router: Manages traffic between subnets and the internet.
- Internet Gateway: Necessary for the NAT Gateway to send traffic to the internet.
- Public Subnet: Hosts the NAT Gateway, which has a public IP.
- Private Subnet: Contains resources without public IPs.
- Route Table: Configures the private subnet to route outbound traffic (
0.0.0.0/0) through the NAT Gateway.
Example Use Case:
- Backend servers or databases that need internet access for updates or patches but shouldn't be accessible from the internet.
Security Considerations:
- Private Subnets: Resources lack public IPs, reducing exposure to external threats.
- Security Groups: Allow inbound traffic only from specific sources (like your application servers) and block everything else.
- Monitoring: Keep an eye on NAT Gateway logs for any unusual outbound activity that might indicate a security issue.
Key Differences: Internet Gateway vs. NAT Gateway
| Aspect | Internet Gateway | NAT Gateway |
|---|---|---|
| Purpose | Enables public-facing resources to access and be accessed by the internet. | Allows private resources to access the internet without being exposed to inbound traffic. |
| Subnet Type | Public | Private |
| Traffic Direction | Bi-directional (inbound and outbound) | Outbound-only (blocks inbound traffic) |
| Security Posture | Higher risk due to public exposure | More secure as resources remain private |
| Use Cases | Web servers, public APIs | Backend servers, databases needing updates |
Security Best Practices
- Minimize Public Resources: Only place resources that need to be internet-facing in public subnets.
- Leverage Private Subnets for Sensitive Data: Keep databases and internal applications in private subnets behind a NAT Gateway.
- Monitor and Audit: Use AWS tools like CloudTrail, VPC Flow Logs, and GuardDuty to watch for suspicious activity.
- Principle of Least Privilege: Configure Security Groups and NACLs to allow only necessary traffic.
- Optimize Costs: Be aware that NAT Gateways incur charges. For cost-saving, consider NAT instances if appropriate.
Conclusion
Choosing between an Internet Gateway and a NAT Gateway is vital for building a secure and efficient AWS environment. If you're running public-facing applications, an Internet Gateway is the way to go—but be mindful of the increased security risks. For private resources that need internet access without exposure, a NAT Gateway is your best bet, aligning with security best practices.
By thoughtfully applying these gateways and adhering to robust security measures, you can design a VPC architecture that not only meets your organization's needs but also keeps your cloud resources secure.